Sunday, November 23, 2008
What is a Motherboard?
The motherboard is the main circuit board inside your PC. Every components at some point communicates through the motherboard, either by directly plugging into it or by communicating through one of the motherboards ports. The motherboard is one big communication highway. Its purpose inside your PC is to provide a platform for all the other components and peripherals to talk to each other.

Types of Motherboards
The type of motherboards depends on the CPU it was designed for. You can therefore categories motherboards by which socket type they have. e.g. Socket A, Socket 478 etc. The Type of motherboard you buy is very important, as it will need to house your CPU, and they are not interchangeable. When buying a motherboard, it will always tell you what socket type it has.When Buying a Motherboard
As everything you have on the PC at some point needs the motherboard, you need to consider these components when buying a motherboard. Foe example, if you have a lot of devices with a PCI interface that you wish to use, there is little point buying a motherboard that only offers you 3 PCI slots. Like wise with memory, you have to make sure that there are enough slots for the amount of memory you have or wish to have.
The motherboard also needs the correct type of interface for your Memory, Graphics card, Hard disks and other items as well. You will find that most motherboards offer everything you need however it needs checking on when buying. Its especially important to pay detail to your motherboard if you want to use older components, which a new motherboard may or may not support.
The major difference between motherboards that support the same CPU is the model of the chipset (more on the chipset later). Different chipsets offer different performance and different features in terms of memory support, AGP port speed, Multiplier numbers, Bus speeds and much more.
Speed of a Motherboard
Motherboards have got to be one of the hardest components to measure the speed of. Performance can really only be measured by benchmarking using the same components in several motherboards of the same type. You often find that motherboards with the same chipset have roughly the same performance in real world tests. The minor differences that do occur are down to the quality of the materials used and the quality of the manufacturing.
The Motherboards speeds that are quoted on the box are maximum supported speeds for other components. For example motherboards will quote the maximum FSB (Front Side Bus) speed. However without a CPU that also supports this speed, it will never be reached. Likewise when it quotes the maximum memory speed. The memory of this speed has to be present.
What is a Motherboard Chipset?
A motherboard chipset controls all the data that flows through the data channels (buses) of the motherboard. The primary function of the motherboard chipset is to direct this data to the correct area's of the motherboard, and therefore the correct components.
Components of a Motherboard
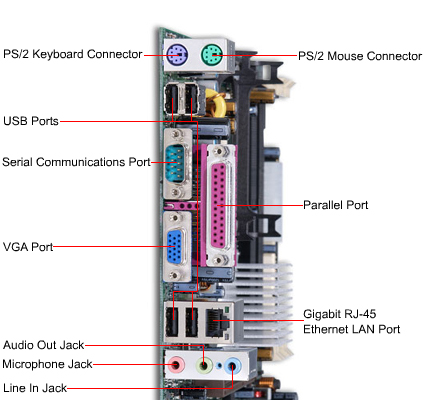
The motherboard contains many connections for all type of components. Motherboards contain expansion slots such as the ISA, PCI, AGP and DIMM sockets. It also contains external connections for your onboard sound card, USB ports, Serial and Parallel ports, PS/2 ports for your keyboard and mouse as well as network and Firewire connections.
So the motherboard has a massive part to play in the workings of your PC. Components that you buy all rely on the motherboard to have the correct connections are available and working. Its best to buy a decent motherboard especially if you plan on buying extra's in the future.
Did You Know?
- Most computer dealers say they build their computers. If they carry a 3 year warranty they are built by someone else or the warranty is out of their back pocket. Very few parts outside of monitors carry anything pass one year, a few motherboards and even less hardrives carry a 3 year warranty.
- Integrated Motherboard: A motherboard where some or all of the internal input or output devices are soldered into it.
- Motherboard was the original name of the what is now called "main board." The difference is that motherboards had "daughter boards" plugged into them. These "daughter boards" later became simply "cards." Most brands of "main boards" have no cards, some don't even have plug-in slots for such.
- Integrated motherboards cause problems when wanting to upgrade your computer, also, LOTS more money. EXAMPLE: Most Compaq /HPs, Dells, Gateways, IBMs have only three pieces usable in an upgrade: the CD ROM ($25 new), hard drive (usually too small to be used, $65-$95 new) and the 3.5" drive ($10 new).
- The motherboard is the main board in a computer that supports the processor (CPU) and all internal input and output devices. Input and output devices are the video, modem, sound card, hard drive and floppy controllers, memory (RAM), network cards. All modern PCI motherboards, thanks to Intel, contain integrated floppy and IDE hard drive controllers. Again thanks to Intel & Via almost all motherboard now have integrated sound also. Luckily we can disable the on-board sound and put in a real Sound Blaster sound card.
- Compaq/HP, Gateway, Acer, IBM, Pionex, Dell, NEC, Sony and Packard Bell computers make good landfill after crushing. That is if they have biodegradable motherboards. A case of Samsung and most Maxtor hard drives make fair boat anchors.
Scams
On-line auctions are now the number one location where thefts and scams will occur. If at all possible look at the sellers history or profile. Always remember if it sounds to be good to true, it probably is.Piracy
With the advances in technology it is now possible for anyone to make their own CDs it is possible that you may be buying copied software which is illegal. Ensure that the software you are buying is a authentic copy, documentation is included with the software, and the the CD does not appear to be burned. Generally burned CDs will have a unusual color such as green or gold tint. However it is still possible for someone to make CDs which can look like an ordinary CD. Another way of possibly determining if Illegal copy is the price. If for example you see a Adobe Photoshop 5.0 for $20-$70 dollars its more then likely not a authentic copy. If it sounds to be good to be true it probably is.On-line Auctions
Companies such as E-bay or Yahoo may provide auctions which other people have the capability of listing products that they are selling. We recommend that if you purchase through an an auction that you only pay by check to prevent possible credit card fraud. If you need to user your credit card consider such options as PayPal.Return Policy
Ensure that the you verify what the resellers return policy may be incase the device is not functioning or is not compatible with your computer.Extra Note: Generally software cannot be returned to the place of purchase to help prevent software piracy.
Warranty
Verify the warranty on the product insuring that it is either provided by the manufacture of the product or the place of purchase.CPU Compatible
There are a wide variety of different types of CPU Sockets and Slots. When looking at purchasing a motherboard ensure it is compatible with the CPU you have or that it will be compatible with the CPU you plan on purchasing.Upgrade
Upgrading a motherboard on the computer allows for new improved hardware to be added into the computer.Upgrade
Upgrading a motherboard on the computer will speed up the overall performance of the computer. May not be noticeable.P4 System Optimization During Installation
When you install OS (other than WinXP) on an Intel 845 or 850 chipset based Pentium4 system, you need to install the chipset driver before any other drivers, such as video card and sound card. Here's the installation order.- OS (Win2000, 9x, Me)
- Service Pack (if necessary)
- Chipset Driver (usually in the CD that comes with your motherboard)
- Drivers for Other Devices
ASUS P4T + 1GB RDRAM + Win9X/Me = Not Good
Currently, ASUS P4T motherboards with 1GB of populated RDRAM will not work within a Windows 9X/Me environment. This is not much of a tragedy since there is no particular reason to have 1GB of RAM on a Win9X/Me system -- they only offer performance gains up to 512MB. However, this may cause problems for people intending to do dual-boot systems, so be aware.General P4 Guidelines
P4 systems currently require RDRAM memory (Rambus, RIMM..). The P4 platform will supposedly support SDRAM by the end of 2001.General P4 Guidelines
Boxed CPUs come with 2 x 64MB (total of 128MB) RIMM. These are not ECC. Intel may begin packaging 2 x 128MB RIMMs in the future.General P4 Guidelines
RDRAM can be PC600, 700 or 800. The modules that come with the CPU are PC800, the fastest type.General P4 Guidelines
Memory has to be installed as a pair. That's why the CPU comes with 2 x 64MB, instead of 1 x 128MB. The pair of the memory has to be the same size, type (ECC or non-ECC) and speed (PC600 or PC800).General P4 Guidelines
The case has to have 4 specific holes to support a big heatsink. An Antec case (#A58) and a mid tower case (#A51) have the holes. The new aluminum cases do as well.General P4 Guidelines
P4 motherboards have a new 12V connection. In order to use P4 with a regular power supply (without the 12V connector), you need to use a PC Power&Cooling 12VATX adapter. This will convert the regular power connection to 12VATX connection. Or, you can replace the power supply with one that already has the 12VATX connection.Microsoft Windows 2000 Patch for AGP Applications on AMD Athlon and AMD Duron Processors
AMD says, "An issue has been identified that could result in the corruption of video data shared between AGP graphics adapters and AMD Athlon or AMD Duron processors when running Microsoft Windows 2000. This issue is independent of system chipset and has been observed when running Ziff-Davis 3D Winbench 2000 and Mad Onion 3DMark 2000 in benchmarking mode. AMD and Microsoft have worked together to identify a patch that involves adding a key to the registry. To add the key run the registry key installation file below or add the registry key as detailed in Microsoft KnowledgeBase article Q270715. AMD recommends that AMD Athlon and AMD Duron users with AGP graphics adapters running Windows 2000 install this patch.Introduction
Consider the desk-and-file-cabinet metaphor for a moment. Imagine what it would be like if every time you wanted to look at a document or folder you had to retrieve it from the file drawer. It would slow you down tremendously, not to mention drive you crazy. With adequate desk space - our metaphor for memory - you can lay out the documents in use and retrieve information from them immediately, often with just a glance. Here's another important difference between memory and storage: the information stored on a hard disk remains intact even when the computer is turned off. However, any data held in memory is lost when the computer is turned off. In our desk space metaphor, it's as though any files left on the desk at closing time will be thrown away.Did You Know?
- For years, computer scientists and marketing types have abused the metric system when it comes to quantifying things like computer memory, disk space, etc. The reason for this is that in general computers are binary systems, and they work with powers of two. For the most part, this works fine, but once you start counting high enough, it becomes cumbersome to say that your computer has 1,073,741,824 (230) bytes of memory in it. So, it became common practice to shorten things by using the metric prefixes "kilo", "mega", "giga", "tera", etc.
- To boost performance, (In most cases); Bigger and better RAM would be a better upgrade as opposed to bigger and better CPU.
- In many cases same amount of RAM chips can still have difference in performance depending on thier bus speed. This bus speed is expressed in Megahertz as in 133MHz.
Win9x
If you're running Windows 9x or higher and have less than 64 megs of RAM, go out and buy more. I hate to say it, but it's the truth.Don't Mix and Match
It's important not to mix different types of memory modules in your PC. Most PCs have three DIMM sockets on their motherboards, and one or two of them are usually free. Adding RAM is as simple as plugging in new DIMMs.DIMM of the Day
RAM is sold in the form of chips contained on small circuit boards called memory modules. If your current desktop PC was manufactured in the last three or four years, it most likely uses 168-pin DIMMs (dual in-line memory modules). DIMMs vary depending on their capacity (16MByte, 32MByte, 64MByte, and 128MByte), the PC's bus speed, the type of RAM chips they contain, and other factors. You can usually determine what type of DIMM your PC uses by consulting the PC's manual or by calling the manufacturer's technical support line.SIMMS Like Old Times
If your PC is more than three or four years old, it probably uses SIMMs (single in-line memory modules). Though the examples of memory modules shown in the accompanying photos are DIMMs, the process of upgrading SIMMs is similar. The differences are that SIMMs pivot rather than plug into their slots, and they must be installed in pairs. Most PCs today require a type of memory called PC-100 (100MHz) SDRAM, though slightly older systems need PC-66 (66MHz SDRAM), and somewhat newer systems depend on PC-133 (133MHz VC SDRAM). Some brand-new high-performance systems use a new type of memory known as RDRAM (Rambus DRAM), which currently costs considerably more than DIMMs. Another new type of memory, known as DDR (double data rate) SDRAM, is showing up in some high-speed PCs, mainly those that use AMD processors. To find out more, check out www.rambus.com or www.ami2.org.Faulty Memory
Blue screens during the install procedure of Windows 2000 or XP. This is one of the surest signs of faulty memory.Faulty Memory
Random crashes or blue screens during the running of 2000 or XP is another sign of faulty memory. Note that heat can also be a culprit in the case of general flakiness like this, so you should test for that possibility too.Faulty Memory
Crashes during memory intensive operations. 3D games, benchmarks, compiling, Photoshop, etc.Faulty Memory
Distorted graphics on screen. This can also be related to the video card.Faulty Memory
Failure to boot. This can be accompanied by repeated long beeps, which is the accepted BIOS beep code for a memory problem. In this circumstance, you cannot test the memory with diagnostic software, so your only option is testing by replacement, either at home or at your computer dealer.What is Computer Hard Drive?
A hard drive is a mass storage device found in all PCs (with some exclusions) that is used to store permanent data such as the operating system, programs and user files.
The data on hard drives can be erased and/or overwritten, the hard drive is classed as a non-volatile storage device which means it doesn't require a constant power supply in order to retain the information stored on it (unlike RAM).
Inside every hard drive are small round disk-like objects made of either an aluminum/alloy or a glass/ceramic composite, these are called platters, each platter is coated with a special magnetic coating enabling them to store data magnetically.
Hovering above these platters are read/write heads that transfer data to and from the platters.
Hard Drive Capacities
Hard drives come with many different storage capacities, hard drive capacity is measured in bytes, with common capacities being stated in MB (Megabytes) and GB (Gigabytes).
To understand these figures correctly you need to know the basics of how data is stored/processed in digital systems such as PCs.
Digital data is a series of 1's (ones) and 0's (zeros) which are referred to as bits (Binary digITS), a byte is made up of 8 of these bits, so a single byte of data may look like 01001011 (8 consecutive bits).
- 1 Bit = either a 0 (zero) or a 1 (one)
- 1 Byte = 8 bits
- 1 KB (Kilobyte) = 1024 bytes (210)
- 1 MB (Megabyte) = 1024 Kilobytes (220)
- 1 GB (Gigabyte) = 1024 Megabytes (230)
- 1 TB (Terabyte) = 1024 Gigabytes (240)
In the old days it was common to find hard drives with a capacity of just 5MB, nowadays it is hard to buy a new hard drive with less than 40GB, that's 40,960 Megabytes !
Common hard drive capacities these days range from 40GB up to and exceeding 120GB.
As a real world example let's take a color photo, and let's say the photo takes up 500 Kilobytes of storage space on a hard drive, so if you had a 40GB hard drive you could potentially store up to 81,290 color photos.
This is obviously hypothetical due to the fact that on the hard drive you would need your operating system and programs which would take up some of the storage space, but you can see the point.
When you consider that an average letter written in a word processor is around 30KB it becomes apparent that the storage capacity of modern hard drives is massive!
Hard Drive RPM Speeds
You will often see hard drives advertised as being capable of a certain RPM (Revolutions Per Minute), this figure (as the name suggests) refers to how many times the spindle makes a complete 360? turn in any single minute.
The higher the RPM, the faster the data can be read from the platters, which increases overall performance.
RPM values range from about 5,400RPM to 12,000RPM and above.
Did You Know?
- The very first production hard disk was the IBM 305 RAMAC (Random Access Method of Accounting and Control), introduced on September 13, 1956.
- IBM 305 RAMAC had approximately five megabytes capacity.
- The first hard disk drive designed in the 5.25" form factor used in the first PCs was the Seagate ST-506. It featured four heads and a 5 MB capacity. IBM bypassed the ST-506 and chose the ST-412--a 10 MB disk in the same form factor--for the IBM PC/XT, making it the first hard disk drive widely used in the PC and PC-compatible world.
"I see all these terms like "bytes", "megabytes" and kilobytes. I don't know a kilobyte from a dog bite. How are the size of files measured, anyway?"
A bit (short for "binary digit") is the smallest possible unit of information on a PC. A single bit can hold only one of two values: 0 or 1.A byte (short for "binary term") is a unit of storage capable of holding a single character. On almost all modern computers, a byte is equal to 8 bits.
A kilobyte (KB) is 1,024 bytes.
A megabyte (MB) is 1,048,576 bytes, or 1024 kilobytes.
A gigabyte (GB) is 1,073,741,824 bytes, or 1024 megabytes.
A terabyte (TB) is 1,099,511,627,776 bytes, or 1024 gigabytes.
A floppy disk that can hold 1.44 megabytes, for example, is capable of storing approximately 1.4 million characters, or about 3,000 pages of information. An 8.4 gigabyte hard drive can store about 9 billion characters and can hold close to 18 million pages of information.
I received an error telling me I was low on memory. I checked My Computer and it shows I have plenty of megabytes left. What's the problem?
This is a very common misconception. Although many PC owners use the terms interchangeably, "memory" and "hard drive space" are two night and day different things.Many users tend to confuse the terms "memory" and "drive space" and often use one when they actually mean the other. Extreme examples of this confusion have been folks who get "out of memory" errors and run out and buy hard drives, and those who purchase SIMMs expecting the upgrade to add additional megabytes of storage space in which they can install software programs.
Memory refers to the amount of RAM (Random Access Memory) installed in the PC, whereas hard drive space is referring to the available amount of storage capacity on the PC's hard disk(s).
One analogy that has often been used to clarify the difference that I find works well is to compare the computer to an office that contains a desk, a file cabinet, and a bulletin board.
Storage space on your hard drive is like a "filing cabinet" where work is stored when not in use.
L2 Cache memory is like a "bulletin board" making the work at the "desk" go faster by keeping frequently used items close at hand.
RAM memory is like a "desk" with current work open on it and readily accessible.
Using the analogy above, the file cabinet represents the computer's hard disk, which provides high-capacity storage. This is where your data (work) is stored when not in use. Your memory (RAM) is the desk where what you are working on at the moment is found. When you want to do some work you take the files out of the filing cabinet (i.e. open a program) and put them on the desk.
Upgrading memory is like buying a larger desk. It will give you the ability to work on more files at one time and as there is more room to operate your system will perform a bit better. This does NOT however increase your storage space for files not in use, for that you have to buy a second filing cabinet (hard drive).
Another key difference between memory and hard drive space is that the data stored on a hard disk is not lost when the PC is turned off. This is not the case with memory however, any information held in memory is cleared when the computer is turned off. Again using the office analogy this would be equivalent to saying that any files you leave on your desk after 5PM will be tossed out by the cleaning crew. This is why occasionally saving work in process is such a good idea.
To take our office example yet one step further, if the desk and the filing cabinet helps us to understand the relationship between RAM memory and a PC's hard disk then we can equate secondary (Level 2 or L2) cache memory to a bulletin board we may hang over our desk.
As we go back and forth taking files out of storage in the filing cabinet, working on them at our desk and returning them, we may choose to stick some of the information that we find we are referring to constantly up on our bulletin board. When you need that information rather than going all the way to the filing cabinet all you have to do is to look up on the bulletin board and there it is.
Primary and secondary cache memory serves in much the same way, storing frequently accessed data in a special area so that it is always close at hand and loads much faster when needed.
I bought a 6.4 GB hard drive. When I look at the size of the hard drive by using DriveSpace3 or Right-Clicking on Drive C in My Computer I get a total amount of 5.99 GB. Where is the rest of my space?
This has to do with the way nearly every hard drive manufacturer in existence calculates hard drive size. They all define 1 gigabyte = 1,000,000,000 bytes instead of the 1 gigabyte = 1,073,741,824 bytes which it *really* is.
This is called "binary" vs "decimal" sizes. If you look at the *fine print* you will always see "[Company X] defines 1 gigabyte as 1 billion bytes". This is standard industry practice, unfortunately were a drive manufacturer (Western Digital for example) to be *honest* about this then their drives as advertised would all appear smaller than the competitors, when in fact they would not be. Shoppers would be comparing "apples to oranges" rather than "apples to apples".
Put another way in reality your hard drive is 6400 million bytes rather than 6400 megabytes. A 6.4 GB drive is actually closer to a 6 GB drive when viewed from a *real world* standpoint.
I installed an 8.4GB hard drive on my Aptiva but when I check both DriveSpace3 and the Properties of the drive in My Computer the "pie chart" is one solid color, showing all free space. It also says that the drive is only 2 GB. What up with that?
DriveSpace3 is an older Windows application developed prior to the advent of FAT32, and nobody at Microsoft has chosen to inform it that partitions larger than 2 GB are now not only possible but the norm. DriveSpace compression is not supported under FAT32, this utility is provided only for use under FAT16 anyway.As far as the Properties of hard drives in My Computer and Windows Explorer, on Win95 systems where Internet Explorer version 4.x and the Active Desktop Update have not been installed the Properties figures key off of the inaccurate DriveSpace3 utility. On Windows 98 systems and systems running Win95 OSR2 on which Internet Explorer version 4.x with the Active Desktop update has been installed the "pie chart" in My Computer will be accurate.
What is this "FAT" I keep hearing about? What FAT do I have and what difference does it make?
FAT stands for File Allocation Table. This is what your Windows operating system uses to locate files on your hard disk. Due to fragmentation, a file may be divided into many sections that are scattered around the disk...the FAT keeps track of all these pieces.
The only file system that the original version of Win95 is called VFAT, or FAT16. Windows 98 and the OSR2 versions of Win95 support both FAT16 and the more efficient FAT32.
The advantages of the FAT32 file system are:
Unlike FAT16 where one can create a 2GB maximum partition size one can create any size partition under FAT32
Smaller cluster sizes making for a much more efficient drive on which more files can be stored.
Other than adding a larger or second hard drive what can I do as far as freeing up some space? What can I delete as far as preloaded software? What shouldn't I delete?
Other than that the best thing I can tell is is "when in doubt, Rename":
Wherever possible you always want to uninstall software rather than deleting it outright, but unfortunately on older Aptivas many of the programs IBM preloaded feature no uninstall option at all, often there's no alternative except to delete unwanted programs.
To be 100% safe when deleting anything a good idea is to RENAME the folders you are thinking of deleting pending actual deletion. Right-Click on the folder in Explorer (ex: "CServe") > Click Rename > Change the name by one letter (ex: "XCserve"). This takes the files out of their normal path and "simulates" the effect of deleting the folder.
Run your system normally for a few days. If you get no errors, have no problems and everything works after that time send the folder to the Bin and flush. If you DO have any problems just change the name back.
What is Central Processing Unit (CPU)?
Sometimes we refer to the CPU as the system box or brain. It is the computer chip that does all of the processing for the computer. Inside this tiny chip are millions of transistors (electrical switches) that are connected so they can carry out mathematical calculations. Everything a computer does is essentially a mathematical calculation.
Did You Know?
- The first single chip CPU was the Intel 4004, a 4-bit processor meant for a calculator (not Intel 8086). It processed data in 4 bits, but its instructions were 8 bits long. Program and Data memory were separate, 1K data memory and a 12-bit PC for 4K program memory (in the form of a 4 level stack, used for CALL and RET instructions). There were also sixteen 4-bit (or eight 8-bit) general purpose registers.
The 4004 had 46 instructions, using only 2,300 transistors in a 16-pin DIP. It ran at a clock rate of 740kHz (eight clock cycles per CPU cycle of 10.8 microseconds) - the original goal was 1MHz, to allow it to compute BCD arithmetic as fast (per digit) as a 1960's era IBM 1620.
The 4040 (1972) was an enhanced version of the 4004, adding 14 instructions, larger (8 level) stack, 8K program space, and interrupt abilities (including shadows of the first 8 registers). Should Pioneer 10 and Pioneer 11 ever be found by an extraterrestrial species, the 4004 will represent an example of Earth's technology.
- Then came Intel 8086 (1978) - This chip was skipped over for the original PC, but was used in a few later computers that didn't amount to much. It was a true 16-bit processor and talked with its cards via a 16 wire data connection. The chip contained 29,000 transistors and 20 address lines that gave it the ability to talk with up to 1 MB of RAM. What is interesting is that the designers of the time never suspected anyone would ever need more than 1 MB of RAM. The chip was available in 5, 6,, 8, and 10 MHz versions.
- Intel was not the only manufacturer playing in the sandbox at the time. AMD put out its AM486 series in answer to Intel's counterpart. AMD released the chip in AM486DX4/75, AM486DX4/100, and AM486DX4/120 versions. It contained on-board cache, power management features, 3-volt operation and SMM mode. This made the chip fitting for mobiles in addition to desktops. The chip found its way into many 486-compatibles.
Tips
What benefit does it (MMX) offer users?
MMX technology raises the PC experience to new levels, when software designed for the technology runs on systems based on the new processor. It delivers 10 to 20 percent more processor performance over Pentium processors at the same clock speed due to the microarchitectural enhancements.Additional performance and/or enhancements in quality of graphics, video and sound may be achieved to the extent that the programmer takes advantage of the technology. On the Intel Media Benchmark, which measures multimedia performance, the processor delivers more than 60 percent performance improvement over Pentium processors at equivalent clock speeds.
Power Supply
New CPUs require higher rating power supply. Hence always ensure that your power supply is rated at 350 W at least.Cool It!
Invest in good heatsink and fan combination for your processor.Genuine Article
Always buy Genuine CPU. Check Hologram seal on Intel CPU box. In case of AMD, make sure that the plastic casing is not broken.Cache That Monkey
If you plan to do CPU intensive tasks such as graphic processing, gaming and animation go for CPU with 256 KB or more of L2 cache. The Pentium 4 Northwood has 512 KB of L2 cache. For gaming applications, go for CPU which supports 3DNow! or SSE.Palomino
If power requirement and heat dissipation are not an issue, you can go for cheap and affordable Palomino cores.Save the Money
If you want only basic office applications, you can go for cheap CPU like Cyrix M III processor. This cheap CPU works with any socket 370 motherboard.High End Users
For high end 3D design and CAD applications, you will require a processor with highest clock speed and the largest on board cache memory. Pentium and Athlon processors are best for such type of applications.Intel Based System:
CPU Cooling - COOL your CPU first. Then it will perform. Processor cooling is very important from performance and reliability point of view. Always provide good quality cooling fan with high rated heatsink.Intel Based System:
Extra 12 V Power For Pentium 4 - All Pentium 4 processors require extra 12 volt power supply. Make sure the power supply for new processor has necessary four pin 12 V connector. This connector fits into the ATX 12 V connector on your Motherboard.Intel Based System:
Hyperthread Technology - Intel's 3.06 GHz processor incorporates Hyperthreading technology which gives better CPU performance when running multiple applications simultaneously.Intel Based System:
CPU Type - Willamette CPU's are fabricated using 0.18 micron fabrication process. Willamette requires more power and generate more heat. New Northwood CPU's are fabricated using 0.13 micron fabrication process. Northwood CPU's have L2 cache of 512 KB.Intel Based System:
Intel Drivers - Intel supplies drivers for new 800 series chipsets including 845, 845 - DDR and 850 chipsets called the Intel application accelerator driver. These drivers increase the performance of your IDE devices. They offer better boot times and also surpass 137 GB limitation of the IDE drives in the native Window drivers. SSE2 type of special instructions in Intel CPU's help deliver better performance with certain types of data.AMD Based System:
CPU Cooling - COOL your CPU first. Then it will perform. Processor cooling is very important from performance and reliability point of view. Always provide good quality cooling fan with high rated heatsink. Use thermal paste for better contact between heatsink and CPU. If by chance you forget to connect the fan supply and switch on the motherboard, you will damage the AMD CPU with in seconds. Always use CPU heatsink and fan combination that is certified by AMD.AMD Based System:
Proper Mounting - As bare Silicon is exposed at the top surface in AMD CPU, heatsink installation should be done properly. You should not slide the heatsink on the top surface of CPU. A small scratch or friction may damage CPU.AMD Based System:
Power Supply - It is always better to go for minimum 300 w power supply for AMD based system.AMD Based System:
Special Instructions: The 3DNow! instruction set streamline power of certain applications.AMD Based System:
Memory: You can use SDRAM or DDR memory. SDRAM is cost effective option for basic applications. However for demanding applications ( graphic or high end gaming), go for DDR memory. DDR memory is good for high speed applications.AMD Based System:
Type of Processor - AMD Duron processors offer reasonably good performance with respect to their price. But as they are phased out, it is better to go for Athlon processor. They are available in old 0.18 micron Palomino and new 0.13 micron Thoroughbred core. New technology requires less power and generates less heat. Not all motherboards support them. Hence always ensure that your motherboard supports new CPU before buying the motherboard. Extra check the motherboard manual.What is a Computer Case?
You seriously asking that? :)Ok, dumb question; But did you know that most people don't know that almost all computers (mostly generic) can have thier case exchanged for a better, more efficient, and better ventilated case resulting in a better perfomance and looks for your computer? Well now you do!
Did You Know?- 90% of the heat related problems in all laptops are due to faulty design of the casing.
- Sprucing up your cases vents will give you quite a boost of performance in both your video card and ram
- An awesome looking case that has very minimum ventilation is a bad case!
Tips
Mini Tower
Advantages: Excellent size which can be placed on top of below of a computer desk.Disadvantages: While this case does offer upgradability it can be filled up much faster then the Mid-Sized tower.
Recommendations: Great PC for end-users and small businesses.
Mid-Size Tower
Advantages: Excellent case which can fit below and on top of your computer desk.Plenty of expandability for new devices for businesses, end-users, and advanced users.
One of the most used computer cases found today.
Disadvantages: None
Recommendations: This case is an excellent choice for all users and businesses.
Full-Size Tower
Advantages: Excellent computer for upgradability.Excellent case for a server machine.
Disadvantages: Cost is going to be a lot more then a standard case.
Generally a large case which cannot be placed on top or beneath a desk.
Recommendations: We recommend that this type of case be purchased by advanced users or users who plan to have a stand alone machine as a server.
Desktop
Advantages: Excellent desk computer.Great use of desk space when monitor is placed on top of the computer.
Disadvantages: With some types of desktop cases can be very difficult to upgrade.
Does not really work on the floor.
Recommendations: Excellent choice for a business and home user computer. End users planning to upgrade or place computer on floor we recommend going with tower computer unless manufacturer provides desktop to be converted to tower.
Style
I am getting tired of the standard looking case. I would like to find a case with style and possibly a clear case. Where can I find a company that can supply me a case like this?There are several types of companies that manufacturer cases with more style as well as clear cases. You can find these as well as other case manufacturers on our Pricing Solution.
Introduction
A network is a group of things that are connected together. In a computer network, the things that are connected are computers, of course. A computer network can be as small as two computers but there is no maximum size, and many networks have hundreds or thousands of computers.
There are three main reasons for connecting computers in a network:
- Share information. This can be messages such as e-mail, or it can be files that are stored on one computer and used by someone at a different computer.
- Share resources. A printer that can be accessed from different computer systems is a shared resource. So is an Internet connection used by more than one computer.
- Centralized control. In most offices, the management determines what the computers may be used for and what kind of resources and support they need. This is much easier to deal with if the computers are connected.
Just as there is no limit to the number of systems in a network, there is also no limit to the geographical size of a network. As a practical matter though, there are some structural differences between a network of computers all in the same room, and a network connecting computers in Los Angeles to ones in Sydney Australia.
The most common network includes computers that are close together, usually in the same building or office. This is called a Local Area Network, abbreviated LAN.
The computers in a LAN are usually connected with cable made up of pairs of wires, but faster (and more expensive) cables are made from glass fibers, called fiber optic cable. A network may even use radio waves, in which case it is a wireless LAN.
When the computers being connected are far apart, typically in different cities, it is called a WAN or Wide Area Network. The connection is usually done with special high-speed lines leased from the phone company, but it is also possible to connect over an ordinary phone line using a device called a modem. It’s slow, but possible. Accessing a network through a phone line and modem is called a dial-up connection.
The biggest of all networks is the Internet. The backbone of the Internet consists of powerful computers all over the world with high-speed connections between them. Individual computers such as yours then connect to this backbone through an Internet Service Provider or ISP.
Most LANs in existence today use a technology called Ethernet. In an Ethernet network, every piece of information put on the network is seen by every other computer on the network, and each computer must determine if that information is meant for itself.
To make this work, before the information goes out on the network it is first broken up into small pieces called packets, and each packet has added to it the address of the computer that should receive it. The part of the packet containing the address is called the header.
Header

Packet diagram
Then, each computer looks at the address on each packet that comes by on the network cable, and copies the ones that have the right address. The computer that sent the packet is called the source, and the one that is supposed to receive it is called the destination.
When a packet comes out of the computer that originated it, that packet must have a complete electrical path to every other computer. The simplest way to do this is to have a cable that goes from one computer to the next until it has connected to each one. This is called a bus network.

A bus network is the simplest to explain and draw, but it’s not often the simplest one to use, especially if computers are distributed around various offices in a building, and then get added, taken away, moved around and so forth.
A much more practical way to connect more than a couple of systems is to connect each one to a device called a hub. Each system has a cable that goes from it to the hub, and inside the hub an electrical connection is made between all of the cables. Each place where a cable plugs into the hub is called a port.

5-port hub ports
To create larger networks, hubs can use one or more of their connections to connect to other hubs. This is called a star network, but as far as the electrical signals are concerned, they go from one computer to every other computer, no different than the bus network.

3-hub star network
When networks get really big, with 100s of systems or more, it’s no longer such a good idea to have each computer look at every packet, because almost none of the packets will be for that computer. The large network can be broken up into smaller groups called subnets, and these are connected with a device called a data switch, or just a switch.
Within each subnet, all of the computers still see every packet, and so does the switch. Normally the switch won’t pass those packets on to the other subnets, but if the packet has an address for a destination in another subnet, the switch will pass the packet to the port for that subnet. All of the systems in that subnet will then see the packet, including the system it is actually addressed to. In order to know where to send a packet, the switch must have a table of addresses for each subnet.

Switch with 4 subnets
The simplest form of a switch is called a bridge, and it connects just two subnets. A bridge only needs two ports then, one for each of the subnets.
Sometimes a network will be so big and complex that one switch isn’t enough to connect all of the subnets. In that case the subnet receiving a packet might be connected to a different switch than the subnet where the packet started. This is a more complicated problem, because the switch would need to know not only the packet’s destination, but also where to send it next to make sure it got there.
For this, a smarter device is needed, called a router. The router needs to know not only the subnet addresses, but also the best path, or route, to get from one to another.

Route path diagram
One place where routers are used in a big way is the Internet. If you send a message on the Internet, it might go through many routers before it reaches its destination. And when you surf to a website, all of the graphics and text showing up on your screen had to go through routers to find their way from the web site to your computer.
By the way, every LAN that connects to the Internet becomes a subnet of the Internet, even if it has its own internal subnets.
In addition to the various ways networked systems can be physically connected, there are two basic ways that network activities can be arranged. In one, all of the computers have equal status. This is called peer-to-peer, because a peer means someone (or something) that is the equal of another. Peer-to-peer is used mostly in very small networks of less than a dozen systems.
The more common arrangement is called client-server. One system, called the server, is responsible for a particular activity or resource. The other systems are called clients, and they go through the server when they want to use the function or resource that the server is responsible for.
Some of the things servers are commonly used for include network administration, e-mail, printers, file storage, and Internet access. Often several of these functions will be combined into one machine. There is no rule that says a network server and a print server can’t be the same system.
Clients Server

print server
There is also no rule that says a server must serve the entire network. It is usually convenient to have a separate network server for each subnet. There are other divisions that can occur even within a subnet. Computers that need to share the same resources can be organized into workgroups. With the Windows NT operating system, the LAN can be divided into sections called domains, and each domain needs its own server called a domain controller.
A protocol is an agreed-upon standard for how something will be done. When your mother taught you to chew with your mouth closed and keep your elbows off the table, that was a protocol for proper dining. Computer protocols are the rules for connecting with other computers and exchanging information with them.
Ethernet is a protocol. Earlier we called it a technology, but it is also a set of rules for how that technology is used. If each piece of hardware and software complies with the rules, then information can be correctly transferred from one from one system to another in a LAN.
There are many protocols used in networking. There are some protocols that are used together with other protocols, where each one takes care of different aspects of networking. Sometimes two protocols do the same thing in different ways, and it is necessary to choose one or the other. The important thing is that both systems trying to communicate with each other have matching protocols that they can use.
One very important set of protocols is called TCP/IP. It is important because it is what the creators of the Internet decided would be used for that particular network, which means that any computer that wants to connect to the Internet must also use TCP/IP. TCP/IP stands for Transmission Control Protocol / Internet Protocol.
TCP/IP is actually in two parts. The TCP portion covers the agreements between systems about how they will carry on their ‘conversation’, and the IP portion deals with addressing the packets and routing them.
The TCP part all happens in the background and we don’t really need to concern ourselves with it under normal circumstances. However, in a network that uses TCP/IP, every system must have a unique IP address, and that is something that requires human intervention in one way or another.
An IP address is made up of four sets of numbers separated by periods. An example is:
192.168.42.122
Each of these sets of numbers is called an octet, because they started out as 8-digit binary numbers. By changing them into 3-digit decimal numbers, the whole address is shorter and easier to remember. The highest value for any octet is 255, because the highest number you can make with eight binary digits is equal to 255 in decimal.
In most networks, the first three octets are the same for all systems, and the last octet is different for every machine. If there are more than 255 computers in a network, it is usually divided into smaller subnets.
There are two ways to associate a unique IP address to a specific computer. One way is for the administrator to assign a number, which stays the same unless somebody decides to change it some day. That number is then a static IP address.
The other way is to assign a group of addresses to a server, and let the server hand them out as needed to any system that wants to communicate on the network. This produces a dynamic IP address. It is sometimes important to know which method is in use on a network, because with dynamic addressing, the IP address of a machine may be different each time you try to communicate with it.
The example address 192.168.42.122 is only one digit longer than a phone number with area code, but that’s plenty long enough to give most of us a hard time. It’s much easier for people to remember a name instead of a number, and for this reason computers in a network are also given a unique name. It may be something mundane like Sales14, but at least it’s a name and not a number.
This is not only easier to remember, but it solves the problem of a dynamic address that changes all the time, because the computer name doesn’t normally change. It does create another problem though, because the computers use only the addresses and not the names to keep track of each other. Fortunately there is a part of the TCP/IP protocol called address resolution, and it matches up the names and addresses so things keep rolling smoothly along.
The problem with connecting computers to the Internet is that they are then sharing a network with many other computers from all over the world, and the users of some of those other computers are not such nice folks. Protecting the network and the information on it is one of the most important parts of a network administrator’s job.
One way to protect information is to scramble it so that it appears to be gibberish unless someone has the right ‘key’ to unscramble it. Scrambling it is called encryption, and unscrambling it is called decryption. There are many ways to encrypt information, and of course just as many keys to decrypt it.
Encrypting and decrypting information slows things down a bit, so a decision must be made about when to use it. For packets going around the LAN, it depends on how likely it is that someone will gain unauthorized access to the LAN, called hacking. It also depends on how much damage would be done if that happened. If the threat is severe, encryption can be done not only on the transmitted packets but also to information stored on the disk drive.
For information going over the Internet, encryption is much more important unless it’s all right for the whole world to see the information. If you send your credit card number to a vendor, you must trust that vendor to encrypt and safeguard the information.
A computer virus is a little program that makes copies of itself to send to other computers. It’s very similar in some ways to contagious germs spreading a disease from one person to the next. And like diseases, some of these computer viruses have some really nasty side effects, like wiping out important files in the operating system or filling up the hard drive with garbage data.
As we will discuss a little later, there are ways to keep these virus programs from getting to your computer, but they are not foolproof. A lot of viruses come in attached to e-mail, and then they will mail copies of themselves to everyone in your e-mail address folder. You can’t completely block them without blocking e-mail, and most of us like to get e-mail from our friends and coworkers.
The most important prevention for viruses is to have a good anti-virus program installed on your computer. Norton, McCaffey and Panda are probably the most popular. The next most important thing is to keep the anti-virus software up-to-date, because the delinquents who write virus software are always coming up with new tricks, and the anti-virus companies are just as quickly coming up with new versions to stop them.
If you have ever had a computer that was connected to a local area network, you almost certainly had to type in a user name and password to get network access. It’s two forms of ID, just like when you cash a check at department store.
The network administrator used that identification information to determine what you could and couldn’t do on the network. And there may have been additional passwords to access the company’ customer database, employee payroll records, or files stored on someone else’s computer.
Here are a few tips about passwords:
- First, if you share files on your computer, use password protection for them even if they are available to everyone in the network. That way they can’t be tampered with if a hacker breaks in.
- In choosing a password, never use your name, your birthday or other obvious personal information. The best is a random combination of letters and numbers.
- Commit the password to memory, and if you must write it down, hide it. A password written on a post-it note stuck to your monitor is probably worse than no password at all.
- Don’t give your password to someone you don’t know personally just because they claim to be tech support, the phone company, the police or your long-lost Aunt Matilda. Refer them to the network administrator, or better yet, get their phone number and have the network administrator call them back.
In a building, a firewall is a wall to keep fire from spreading from one area to another. In a computer network, a firewall is a boundary that can block unwanted data packets. The firewall may be program running on the server or router, or it may be a separate piece of hardware or even a complete computer system just for that purpose. In any case, its purpose is to look at all of the packets coming through, and decide which ones can pass and which ones get blocked.
Ports – Several pages ago, we defined a port as the place in a hub that a cable plugs into. There is another completely different kind of thing called a port, and that is a location in a computer’s memory that is used by a device or application to send and receive data. Each application will have one (or more) of these locations for its own use.
For instance, there is a common e-mail program that has port # 110, which means that the program exchanges information with the rest of the system at memory location 110. The popular game called Doom uses port # 666.
When a packet is sent over a network, it will contain not only the destination address, but also the port number of the application that will use it at that destination. One of the ways a firewall controls the packets is by looking at the port number, and only passing packets with ports that are appropriate for the destination. If nobody should be playing Doom on the network’s computers, then it would make sense to block port 666.
Another way a firewall can control traffic is to look at the source of the packet. It can have a ‘prohibited’ list that keeps out packets from certain IP addresses, or it can have an ‘allowed’ list and block everyone who isn’t on it. Ports can be done the same way, with a ‘prohibited’ or ‘allowed’ list of ports.
There is much more to know about security, and about networks in general, if one is to be involved in managing them. The purpose of this paper is to present just enough information to enable you talk with network administrators and to understand their concerns when presenting network products to them. For additional training in this subject, we recommend the Micro2000 A+ and Network+ courses.
What is a Computer Network?
- Every network includes:
- At least two computers Server or Client workstation.
- Networking Interface Card’s (NIC)
- A connection medium, usually a wire or cable, although wireless communication between networked computers and peripherals is also possible.
- Network Operating system software, such as Microsoft Windows NT or 2000, Novell NetWare, Unix and Linux.
Types of Networks:
LANs (Local Area Networks)
WANs (Wide Area Networks)
Internet
With the meteoric rise in demand for connectivity, the Internet has become a communications highway for millions of users. The Internet was initially restricted to military and academic institutions, but now it is a full-fledged conduit for any and all forms of information and commerce. Internet websites now provide personal, educational, political and economic resources to every corner of the planet.
Intranet
MANs (Metropolitan area Networks)
VPN (Virtual Private Network)
Categories of Network:
Network can be divided in to two main categories:
- Peer-to-peer.
- Server – based.
Peer-to-peer networks are good choices for needs of small organizations where the users are allocated in the same general area, security is not an issue and the organization and the network will have limited growth within the foreseeable future.
The term Client/server refers to the concept of sharing the work involved in processing data between the client computer and the most powerful server computer.
The client/server network is the most efficient way to provide:
- Databases and management of applications such as Spreadsheets, Accounting, Communications and Document management.
- Network management.
- Centralized file storage.
Client/server application design also lets the application provider mask the actual location of application function. The user often does not know where a specific operation is executing. The entire function may execute in either the PC or server, or the function may be split between them. This masking of application function locations enables system implementers to upgrade portions of a system over time with a minimum disruption of application operations, while protecting the investment in existing hardware and software.
The OSI Model:
There are seven to get familiar with and these are the physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and the application layer.
- Physical Layer, is just that the physical parts of the network such as wires, cables, and there media along with the length. Also this layer takes note of the electrical signals that transmit data throughout system.
- Data Link Layer, this layer is where we actually assign meaning to the electrical signals in the network. The layer also determines the size and format of data sent to printers, and other devices. Also I don’t want to forget that these are also called nodes in the network. Another thing to consider in this layer is will also allow and define the error detection and correction schemes that insure data was sent and received.
- Network Layer, this layer provides the definition for the connection of two dissimilar networks.
- Transport Layer, this layer allows data to be broken into smaller packages for data to be distributed and addressed to other nodes (workstations).
- Session Layer, this layer helps out with the task to carry information from one node (workstation) to another node (workstation). A session has to be made before we can transport information to another computer.
- Presentation Layer, this layer is responsible to code and decode data sent to the node.
- Application Layer, this layer allows you to use an application that will communicate with say the operation system of a server. A good example would be using your web browser to interact with the operating system on a server such as Windows NT, which in turn gets the data you requested.
Network Architectures:
Ethernet
Fast Ethernet
Token Ring
Various PC vendors have been proponents of Token Ring networks at different times and thus these types of networks have been implemented in many organizations.
FDDI
Protocols:
Although each network protocol is different, they all share the same physical cabling. This common method of accessing the physical network allows multiple protocols to peacefully coexist over the network media, and allows the builder of a network to use common hardware for a variety of protocols. This concept is known as "protocol independence,"
Some Important Protocols and their job:
| Protocol | Acronym | Its Job |
| Point-To-Point | TCP/IP | The backbone protocol of the internet. Popular also for intranets using the internet |
| Transmission Control Protocol/internet Protocol | TCP/IP | The backbone protocol of the internet. Popular also for intranets using the internet |
| Internetwork Package Exchange/Sequenced Packet Exchange | IPX/SPX | This is a standard protocol for Novell Network Operating System |
| NetBIOS Extended User Interface | NetBEUI | This is a Microsoft protocol that doesn’t support routing to other networks |
| File Transfer Protocol | FTP | Used to send and receive files from a remote host |
| Hyper Transfer Protocol | HTTP | Used for the web to send documents that are encoded in HTML. |
| Network File Services | NFS | Allows network nodes or workstations to access files and drives as if they were their own. |
| Simple Mail Transfer Protocol | SMTP | Used to send Email over a network |
| Telnet | Used to connect to a host and emulate a terminal that the remote server can recognize |
Introduction to TCP/IP Networks:
What Is TCP/IP?
The Origins of TCP/IP
Net work Cables and Stuff:
Thick Coaxial Cable
Thin Coaxial Cable
Fiber Optic Cable
Twisted Pair Cables
Unshielded Twisted Pair (UTP)
Shielded Twisted Pair (STP)
-Something else to note about these cables is that they are defined in numbers also. The bigger the number the better the protection from interference. Most networks should go with no less than a CAT 3 and CAT 5 is most recommended.
-Now you know about cables we need to know about connectors. This is pretty important and you will most likely need the RJ-45 connector. This is the cousin of the phone jack connector and looks real similar with the exception that the RJ-45 is bigger. Most commonly your connector are in two flavors and this is BNC (Bayonet Naur Connector) used in thicknets and the RJ-45 used in smaller networks using UTP/STP.
Ethernet Cabling
10Base5, this is considered a thicknet and is used with coaxial cable arrangement such as the BNC connector. The good side to the coaxial cable is the high-speed transfer and cable segments can be up to 500 meters between nodes/workstations. You will typically see the same speed as the 10Base2 but larger cable lengths for more versatility.
10BaseT, the “T” stands for twisted as in UTP (Unshielded Twisted Pair) and uses this for 10Mbps of transfer. The down side to this is you can only have cable lengths of 100 meters between nodes/workstations. The good side to this network is they are easy to set up and cheap! This is why they are so common an ideal for small offices or homes.
100BaseT, is considered Fast Ethernet uses STP (Shielded Twisted Pair) reaching data transfer of 100Mbps. This system is a little more expensive but still remains popular as the 10BaseT and cheaper than most other type networks. This on of course would be the cheap fast version.
10BaseF, this little guy has the advantage of fiber optics and the F stands for just that. This arrangement is a little more complicated and uses special connectors and NIC’s along with hubs to create its network. Pretty darn neat and not to cheap on the wallet.
An important part of designing and installing an Ethernet is selecting the appropriate Ethernet medium. There are four major types of media in use today: Thickwire for 10BASE5 networks, thin coax for 10BASE2 networks, unshielded twisted pair (UTP) for 10BASE-T networks and fiber optic for 10BASE-FL or Fiber-Optic Inter-Repeater Link (FOIRL) networks. This wide variety of media reflects the evolution of Ethernet and also points to the technology's flexibility. Thickwire was one of the first cabling systems used in Ethernet but was expensive and difficult to use. This evolved to thin coax, which is easier to work with and less expensive.
Network Topologies:
What is a Network topology?
There are three topology’s to think about when you get into networks. These are the star, rind, and the bus.
Star, a ring topology features a logically closed loop. Data packets travel in a single direction around the ring from one network device to the next. Each network device acts as a repeater, meaning it regenerates the signal
Ring, in a star topology each node has a dedicated set of wires connecting it to a central network hub. Since all traffic passes through the hub, the hub becomes a central point for isolating network problems and gathering network statistics.
Bus, the bus topology, each node (computer, server, peripheral etc.) attaches directly to a common cable. This topology most often serves as the backbone for a network. In some instances, such as in classrooms or labs, a bus will connect small workgroups
Collisions:
Minimizing collisions is a crucial element in the design and operation of networks. Increased collisions are often the result of too many users on the network, which results in a lot of contention for network bandwidth. This can slow the performance of the network from the user's point of view. Segmenting the network, where a network is divided into different pieces joined together logically with a bridge or switch, is one way of reducing an overcrowded network.
Ethernet Products:
Transceivers
For Fast Ethernet networks, a new interface called the MII (Media Independent Interface) was developed to offer a flexible way to support 100 Mbps connections. The MII is a popular way to connect 100BASE-FX links to copper-based Fast Ethernet devices.
Network Interface Cards:
Many NIC adapters comply with Plug-n-Play specifications. On these systems, NICs are automatically configured without user intervention, while on non-Plug-n-Play systems, configuration is done manually through a setup program and/or DIP switches.
Cards are available to support almost all networking standards, including the latest Fast Ethernet environment. Fast Ethernet NICs are often 10/100 capable, and will automatically set to the appropriate speed. Full duplex networking is another option, where a dedicated connection to a switch allows a NIC to operate at twice the speed.
Hubs/Repeaters:
Ethernet hubs are necessary in star topologies such as 10BASE-T. A multi-port twisted pair hub allows several point-to-point segments to be joined into one network. One end of the point-to-point link is attached to the hub and the other is attached to the computer. If the hub is attached to a backbone, then all computers at the end of the twisted pair segments can communicate with all the hosts on the backbone. The number and type of hubs in any one-collision domain is limited by the Ethernet rules. These repeater rules are discussed in more detail later.
| Network Type | Max Nodes Per Segment | Max Distance Per Segment |
| 10BASE-T 10BASE2 10BASE5 10BASE-FL | 2 30 100 2 | 100m 185m 500m 2000m |
Adding Speed:
Bridges:
Bridges are also called "store-and-forward" devices because they look at the whole Ethernet packet before making filtering or forwarding decisions. Filtering packets, and regenerating forwarded packets enable bridging technology to split a network into separate collision domains. This allows for greater distances and more repeaters to be used in the total network design.
Ethernet Switches:
It takes more time to examine the entire packet, but it allows the switch to catch certain packet errors and keep them from propagating through the network. Both cut-through and store-and-forward switches separate a network into collision domains, allowing network design rules to be extended. Each of the segments attached to an Ethernet switch has a full 10 Mbps of bandwidth shared by fewer users, which results in better performance (as opposed to hubs that only allow bandwidth sharing from a single Ethernet). Newer switches today offer high-speed links, FDDI, Fast Ethernet or ATM. These are used to link switches together or give added bandwidth to high-traffic servers. A network composed of a number of switches linked together via uplinks is termed a "collapsed backbone" network.
Routers:
What is a network firewall?
Network Design Criteria:
A network using repeaters, for instance, functions with the timing constraints of Ethernet. Although electrical signals on the Ethernet media travel near the speed of light, it still takes a finite time for the signal to travel from one end of a large Ethernet to another. The Ethernet standard assumes it will take roughly 50 microseconds for a signal to reach its destination.
Ethernet is subject to the "5-4-3" rule of repeater placement: the network can only have five segments connected; it can only use four repeaters; and of the five segments, only three can have users attached to them; the other two must be inter-repeater links.
If the design of the network violates these repeater and placement rules, then timing guidelines will not be met and the sending station will resend that packet. This can lead to lost packets and excessive resent packets, which can slow network performance and create trouble for applications. Fast Ethernet has modified repeater rules, since the minimum packet size takes less time to transmit than regular Ethernet. The length of the network links allows for a fewer number of repeaters. In Fast Ethernet networks, there are two classes of repeaters. Class I repeaters have a latency of 0.7 microseconds or less and are limited to one repeater per network. Class II repeaters have a latency of 0.46 microseconds or less and are limited to two repeaters per network. The following are the distance (diameter) characteristics for these types of Fast Ethernet repeater combinations:
| Fast Ethernet | Copper | Fiber |
| No Repeaters One Class I Repeater One Class II Repeater Two Class II Repeaters | 100m 200m 200m 205m | 412m* 272m 272m 228m |
When conditions require greater distances or an increase in the number of nodes/repeaters, then a bridge, router or switch can be used to connect multiple networks together. These devices join two or more separate networks, allowing network design criteria to be restored. Switches allow network designers to build large networks that function well. The reduction in costs of bridges and switches reduces the impact of repeater rules on network design.
Each network connected via one of these devices is referred to as a separate collision domain in the overall network.
Types of Servers:
Device Servers
Print servers, terminal servers, remote access servers and network time servers are examples of device servers which are specialized for particular functions. Each of these types of servers has unique configuration attributes in hardware or software that help them to perform best in their particular arena.
Print Servers
Print servers generally do not contain a large amount of memory; printers simply store information in a queue. When the desired printer becomes available, they allow the host to transmit the data to the appropriate printer port on the server. The print server can then simply queue and print each job in the order in which print requests are received, regardless of protocol used or the size of the job.
Multiport Device Servers
Given its natural translation ability, a multi-protocol multiport device server can perform conversions between the protocols it knows, like LAT and TCP/IP. While server bandwidth is not adequate for large file transfers, it can easily handle host-to-host inquiry/response applications, electronic mailbox checking, etc. And it is far more economical than the alternatives of acquiring expensive host software and special-purpose converters. Multiport device and print servers give their users greater flexibility in configuring and managing their networks.
Whether it is moving printers and other peripherals from one network to another, expanding the dimensions of interoperability or preparing for growth, multiport device servers can fulfill your needs, all without major rewiring.
Access Servers
Network Time Servers
IP Addressing:
Example: 140.179.220.200
It is sometimes useful to view the values in their binary form.
140 .179 .220 .200
10001100.10110011.11011100.11001000
Every IP address consists of two parts, one identifying the network and one identifying the node. The Class of the address and the subnet mask determine which part belongs to the network address and which part belongs to the node address.
Address Classes:
Class A addresses begin with 0xxx, or 1 to 126 decimal.
Class B addresses begin with 10xx, or 128 to 191 decimal.
Class C addresses begin with 110x, or 192 to 223 decimal.
Class D addresses begin with 1110, or 224 to 239 decimal.
Class E addresses begin with 1111, or 240 to 254 decimal.
Addresses beginning with 01111111, or 127 decimal, are reserved for loopback and for internal testing on a local machine. [You can test this: you should always be able to ping 127.0.0.1, which points to yourself] Class D addresses are reserved for multicasting. Class E addresses are reserved for future use. They should not be used for host addresses.
Now we can see how the Class determines, by default, which part of the IP address belongs to the network (N) and which part belongs to the node (n).
Class A -- NNNNNNNN.nnnnnnnn.nnnnnnn.nnnnnnn
Class B -- NNNNNNNN.NNNNNNNN.nnnnnnnn.nnnnnnnn
Class C -- NNNNNNNN.NNNNNNNN.NNNNNNNN.nnnnnnnn
In the example, 140.179.220.200 is a Class B address so by default the Network part of the address (also known as the Network Address) is defined by the first two octets (140.179.x.x) and the node part is defined by the last 2 octets (x.x.220.200).
In order to specify the network address for a given IP address, the node section is set to all "0"s. In our example, 140.179.0.0 specifies the network address for 140.179.220.200. When the node section is set to all "1"s, it specifies a broadcast that is sent to all hosts on the network. 140.179.255.255 specifies the example broadcast address. Note that this is true regardless of the length of the node section.
Private Subnets:
Subnetting an IP Network can be done for a variety of reasons, including organization, use of different physical media (such as Ethernet, FDDI, WAN, etc.), preservation of address space, and security. The most common reason is to control network traffic. In an Ethernet network, all nodes on a segment see all the packets transmitted by all the other nodes on that segment. Performance can be adversely affected under heavy traffic loads, due to collisions and the resulting retransmissions. A router is used to connect IP networks to minimize the amount of traffic each segment must receive.
Subnet Masking
For example, using our test IP address and the default Class B subnet mask, we get:
10001100.10110011.11110000.11001000 140.179.240.200 Class B IP Address
11111111.11111111.00000000.00000000 255.255.000.000 Default Class B Subnet Mask
10001100.10110011.00000000.00000000 140.179.000.000 Network Address
Default subnet masks:
Class B - 255.255.0.0 - 11111111.11111111.00000000.00000000
Class C - 255.255.255.0 - 11111111.11111111.11111111.00000000
CIDR -- Classless InterDomain Routing.
CIDR was invented several years ago to keep the internet from running out of IP addresses. The "classful" system of allocating IP addresses can be very wasteful; anyone who could reasonably show a need for more that 254 host addresses was given a Class B address block of 65533 host addresses. Even more wasteful were companies and organizations that were allocated Class A address blocks, which contain over 16 Million host addresses! Only a tiny percentage of the allocated Class A and Class B address space has ever been actually assigned to a host computer on the Internet.
People realized that addresses could be conserved if the class system was eliminated. By accurately allocating only the amount of address space that was actually needed, the address space crisis could be avoided for many years. This was first proposed in 1992 as a scheme called Supernetting.
The use of a CIDR notated address is the same as for a Classful address. Classful addresses can easily be written in CIDR notation (Class A = /8, Class B = /16, and Class C = /24)
It is currently almost impossible for an individual or company to be allocated their own IP address blocks. You will simply be told to get them from your ISP. The reason for this is the ever-growing size of the internet routing table. Just 5 years ago, there were less than 5000 network routes in the entire Internet. Today, there are over 90,000. Using CIDR, the biggest ISPs are allocated large chunks of address space (usually with a subnet mask of /19 or even smaller); the ISP's customers (often other, smaller ISPs) are then allocated networks from the big ISP's pool. That way, all the big ISP's customers (and their customers, and so on) are accessible via 1 network route on the Internet.
It is expected that CIDR will keep the Internet happily in IP addresses for the next few years at least. After that, IPv6, with 128 bit addresses, will be needed. Under IPv6, even sloppy address allocation would comfortably allow a billion unique IP addresses for every person on earth
Examining your network with commands:
PING is used to check for a response from another computer on the network. It can tell you a great deal of information about the status of the network and the computers you are communicating with.
Ping returns different responses depending on the computer in question. The responses are similar depending on the options used.
Ping uses IP to request a response from the host. It does not use TCP
.It takes its name from a submarine sonar search - you send a short sound burst and listen for an echo - a ping - coming back.
In an IP network, `ping' sends a short data burst - a single packet - and listens for a single packet in reply. Since this tests the most basic function of an IP network (delivery of single packet), it's easy to see how you can learn a lot from some `pings'.
To stop ping, type control-c. This terminates the program and prints out a nice summary of the number of packets transmitted, the number received, and the percentage of packets lost, plus the minimum, average, and maximum round-trip times of the packets.
Sample ping session
PING localhost (127.0.0.1): 56 data bytes
64 bytes from 127.0.0.1: icmp_seq=0 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=1 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=2 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=3 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=4 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=5 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=6 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=7 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=8 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=9 ttl=255 time=2 ms
localhost ping statistics
10 packets transmitted, 10 packets received, 0% packet loss
round-trip min/avg/max = 2/2/2 ms
meikro$
The Time To Live (TTL) field can be interesting. The main purpose of this is so that a packet doesn't live forever on the network and will eventually die when it is deemed "lost." But for us, it provides additional information. We can use the TTL to determine approximately how many router hops the packet has gone through. In this case it's 255 minus N hops, where N is the TTL of the returning Echo Replies. If the TTL field varies in successive pings, it could indicate that the successive reply packets are going via different routes, which isn't a great thing.
The time field is an indication of the round-trip time to get a packet to the remote host. The reply is measured in milliseconds. In general, it's best if round-trip times are under 200 milliseconds. The time it takes a packet to reach its destination is called latency. If you see a large variance in the round-trip times (which is called "jitter"), you are going to see poor performance talking to the host
NSLOOKUP
It is very important when troubleshooting problems on a network that you can verify the components of the networking process. Nslookup allows this by revealing details within the infrastructure.
NETSTAT
IPconfig
This command when used with the /all switch, reveal enormous amounts of troubleshooting information within the system.
Windows 2000 IP Configuration
Host Name . . . . . . . . . . . . : cowder
Primary DNS Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Broadcast
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . :
WAN (PPP/SLIP) Interface
Physical Address. . . . . . . . . : 00-53-45-00-00-00
DHCP Enabled. . . . . . . . . . . : No
IP Address. . . . . . . . . . . . : 12.90.108.123
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . : 12.90.108.125
DNS Servers . . . . . . . . . . . : 12.102.244.2
204.127.129.2
Traceroute
$ traceroute www.berkeley.edu
traceroute to amber.Berkeley.EDU (128.32.25.12), 30 hops max, 40 byte packets
1 sf1-e3.wired.net (206.221.193.1) 3.135 ms 3.021 ms 3.616 ms
2 sf0-e2s2.wired.net (205.227.206.33) 1.829 ms 3.886 ms 2.772 ms
3 paloalto-cr10.bbnplanet.net (131.119.26.105) 5.327 ms 4.597 ms 5.729 ms
4 paloalto-br1.bbnplanet.net (131.119.0.193) 4.842 ms 4.615 ms 3.425 ms
5 sl-sj-2.sprintlink.net (4.0.1.66) 7.488 ms 38.804 ms 7.708 ms
6 144.232.8.81 (144.232.8.81) 6.560 ms 6.631 ms 6.565 ms
7 144.232.4.97 (144.232.4.97) 7.638 ms 7.948 ms 8.129 ms
8 144.228.146.50 (144.228.146.50) 9.504 ms 12.684 ms 16.648 ms
9 f5-0.inr-666-eva.berkeley.edu (198.128.16.21) 9.762 ms 10.611 ms 10.403 ms
10 f0-0.inr-107-eva.Berkeley.EDU (128.32.2.1) 11.478 ms 10.868 ms 9.367 ms
11 f8-0.inr-100-eva.Berkeley.EDU (128.32.235.100) 10.738 ms 11.693 ms 12.520 ms




